Mini AirSniff is a portable traffic analyzer and penetration testing box.
Disclaimer:
I am not responsible for any damages of any kind. If you follow this guide it is at your own risk.
This guide is for study purposes only.
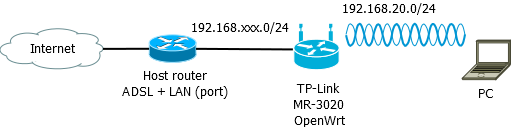
This method is based on allowing a PC to connect to the TL-MR3020 via wifi, to be able to use the internet and through appropriate software such as tcpdump capture all the traffic generated.
The distribution used to perform all the operations was Debian Testing.
Hardware Required:
Tp-Link TL-MR3020
4Gb USB flash drive (Cruzer Fit is recommended for its small size)
Partition the USB flash drive as follows:
Partition 1: Linux Swap Device
Partition 2: ext4
Insert the USB stick into the router
Download the OpenWrt image for the TP-Link MR3020 from
http://downloads.openwrt.org/attitude_adjustment/12.09/ar71xx/generic/
Download the files:
openwrt-ar71xx-generic-tl-mr3020-v1-squashfs-factory.bin
openwrt-ar71xx-generic-tl-mr3020-v1-squashfs-sysupgrade.bin
Download the files needed for the configuration of airsniff:
http://www.hangelot.eu/immagini/airsniff.tar
The premise is that you already have any version of openwrt already installed and that you have ssh active by enabling the system password with passwd.
connect via ssh to the system:
ssh root@192.168.1.1
in the OpenWrt terminal go to the tmp directory:
cd /tmp
Open a new terminal and go to the directory where the files were downloaded
run this command:
rcp openwrt-ar71xx-generic-tl-mr3020-v1-squashfs-factory.bin root@192.168.1.1:/tmp/
now flash the rom:
mtd -r write /tmp/openwrt-ar71xx-generic-tl-mr3020-v1-squashfs-factory.bin firmware
when it reboots connect to the system again:
telnet 192.168.1.1
enable ssh by assigning a new password:
passwd
now copy the sysupgrade to openwrt:
rcp openwrt-ar71xx-generic-tl-mr3020-v1-squashfs-sysupgrade.bin root@192.168.1.1:/tmp/
start the sysupgrade:
sysupgrade -v /tmp/openwrt-ar71xx-generic-tl-mr3020-v1-squashfs-sysupgrade.bin
wait for the system to reboot and then reconnect via ssh.
ssh root@192.168.1.1
Copy airsniff.tar to /usr/share
From a new terminal go to the directory on your PC where the airsniff.tar file is located.
Run this command:
rcp airsniff.tar root@192.168.1.1:/usr/share
From the Openwrt terminal type:
cd /usr/share
tar -xf airsniff.tar
Copy the MAC ADDRESS of the wireless card to be able to insert it in the new configuration file to do this we enable the wifi option from the file /etc/config/wireless
in /etc/config/wireless
you will find a line that says:
# REMOVE THIS LINE TO ENABLE WIFI
option disabled 1
Insert the # as shown here:
# REMOVE THIS LINE TO ENABLE WIFI
# option disabled 1
Save with :wq! and press enter.
Run these commands:
wifi
ifconfig wlan0
Copy the mac Address to a text file.
Run these commands:
cd /usr/share/airsniff
cp -f /etc/config/dhcp /etc/config/dhcp.orig
cp -f /etc/config/firewall /etc/config/firewall.orig
cp -f /etc/config/fstab /etc/config/fstab.orig
cp -f /etc/config/network /etc/config/network.orig
cp -f /etc/opkg.conf /etc/opkg.conf.orig
cp -f /etc/profile /etc/profile.orig
cp -f /etc/config/wireless /etc/config/wireless.orig
cp -f ./dhcp.0 /etc/config/dhcp
cp -f ./firewall.0 /etc/config/firewall
cp -f ./fstab.0 /etc/config/fstab
cp -f ./network.0 /etc/config/network
cp -f ./opkg.conf.0 /etc/opkg.conf
cp -f ./profile.0 /etc/profile
cp -f ./wireless.0 /etc/config/wireless
Edit the file /etc/config/wireless
vi /etc/config/wireless
Insert the MAC address in the line:
option macaddr 'insert your mac here'
Save with :wq! and press enter.
Check that wlan0 has the assigned IP address by running these commands:
wifi
ifconfig wlan0
now turn off the router, connect the cable to the local network and start it again.
wifi network is now 192.168.20.0/24
Connect to the router via wifi, from the shell type the command:
ssh root@192.168.20.1
Now run these commands:
cd /usr/share/airsniff
opkg update
opkg install kernel
opkg install kmod-usb-storage
opkg install kmod-fs-ext4
opkg install block-mount
mkdir /mnt/usb
/etc/init.d/fstab enable
/etc/init.d/fstab start
ls /mnt/usb
check that the usb stick is mounted via “mount” or “df”
Run these commands:
cd /usr/share/airsniff
ln -s /mnt/usb /opt
ln -s /etc /mnt/usb/etc
opkg update
opkg install netcat
opkg -dest usb install tar
opkg -dest usb install openssh-sftp-client
opkg -dest usb install nmap
opkg -dest usb install tcpdump
opkg -dest usb install aircrack-ng
opkg -dest usb install kismet-client
opkg -dest usb install kismet-server
opkg -dest usb install perl
opkg -dest usb install openvpn
opkg -dest usb install n



Use the share button below if you liked it.
Your click is my virtual high-five.